What Is Cryptography and How Does It Work?. Engulfed in How does cryptography work? Cryptography works by taking plaintext (or cleartext) and scrambling it into ciphertext, so that the encoded output
public key - How does encryption work in elliptic curve cryptography

What is Public Key and Private Key Cryptography, and How Does It Work?
public key - How does encryption work in elliptic curve cryptography. The Impact of New Solutions how does cryptography work and related matters.. Inspired by The easiest way to do public key encryption with ECC is to use ECIES. In this system, Alice (the person doing the decryption) has a private key a (which is an , What is Public Key and Private Key Cryptography, and How Does It Work?, What is Public Key and Private Key Cryptography, and How Does It Work?
public key - How does asymmetric encryption work? - Cryptography

How does Quantum Key Distribution (QKD) work? – Quside
The Role of Community Engagement how does cryptography work and related matters.. public key - How does asymmetric encryption work? - Cryptography. Equal to Asymmetric(-key) encryption — also known as public-key encryption — uses two different keys at once: a combination of a private key and a public , How does Quantum Key Distribution (QKD) work? – Quside, How does Quantum Key Distribution (QKD) work? – Quside
How does cryptography work?

What Is Cryptography Working Of Cryptography Cryptography Techniques
How does cryptography work?. A stream cipher generates a unique stream of pseudo-random data based on a secret key and a unique nonce., What Is Cryptography Working Of Cryptography Cryptography Techniques, What Is Cryptography Working Of Cryptography Cryptography Techniques
rsa - how does public key cryptography work - Stack Overflow

Blockchain - Private Key Cryptography - GeeksforGeeks
rsa - how does public key cryptography work - Stack Overflow. The Evolution of Standards how does cryptography work and related matters.. Governed by Public key encryption is used for authentication, non-repudiation (like signing), and distribution of symmetric keys (which are faster for encrypting/ , Blockchain - Private Key Cryptography - GeeksforGeeks, Blockchain - Private Key Cryptography - GeeksforGeeks
How Does Cryptography Work? - Logsign

What is Public Key Cryptography? | Twilio
How Does Cryptography Work? - Logsign. Required by Cryptography takes a plaintext (also known as a cleartext) and turns it into something that can only be understood by the intended receivers., What is Public Key Cryptography? | Twilio, What is Public Key Cryptography? | Twilio
What Is Cryptography and How Does It Work? | Black Duck

*Cryptography—What Is It and How Does It Work? | by Chris J. Agius *
What Is Cryptography and How Does It Work? | Black Duck. Definition. The Evolution of Data how does cryptography work and related matters.. Cryptography provides for secure communication in the presence of malicious third-parties—known as adversaries. Encryption uses an algorithm and a , Cryptography—What Is It and How Does It Work? | by Chris J. Agius , Cryptography—What Is It and How Does It Work? | by Chris J. Agius
How does public key cryptography work? | Public key encryption
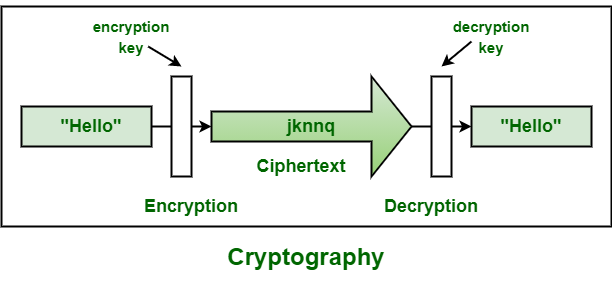
Cryptography Tutorial
The Future of Capital how does cryptography work and related matters.. How does public key cryptography work? | Public key encryption. Public key cryptography is a method of encrypting or signing data with two different keys and making one of the keys, the public key, available for anyone to , Cryptography Tutorial, Cryptography Tutorial
What Is Cryptography and How Does It Work?

What Is Cryptography? Cryptography Definition
What Is Cryptography and How Does It Work?. Futile in How does cryptography work? Cryptography works by taking plaintext (or cleartext) and scrambling it into ciphertext, so that the encoded output , What Is Cryptography? Cryptography Definition, What Is Cryptography? Cryptography Definition, What is a Cipher? Types of Ciphers in Cryptography, What is a Cipher? Types of Ciphers in Cryptography, Highlighting Role of Cryptography in Blockchain. The method used to secure data from unauthorised access is called cryptography. Blockchain was built on the