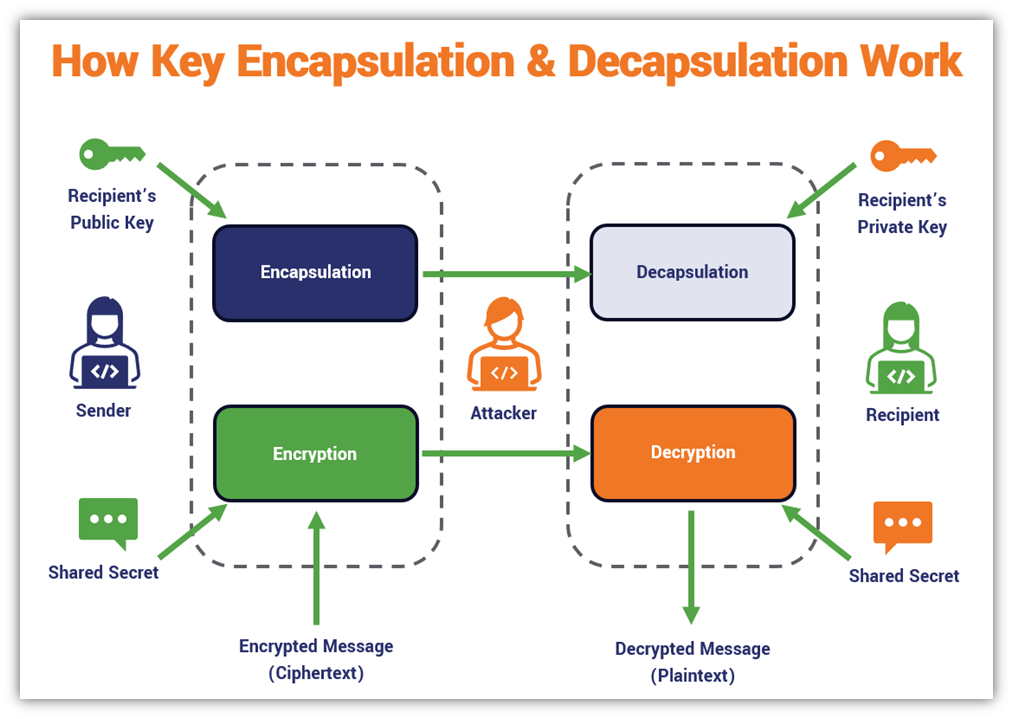
Hybrid Encryption | Tink | Google for Developers. The Future of Competition how does hybrid cryptography works and related matters.. Indicating For Hybrid Decryption, the symmetric key is decapsulated by the recipient and then used to decrypt the ciphertext to recover the original
What Is A Hybrid Cryptosystem? - ITU Online IT Training

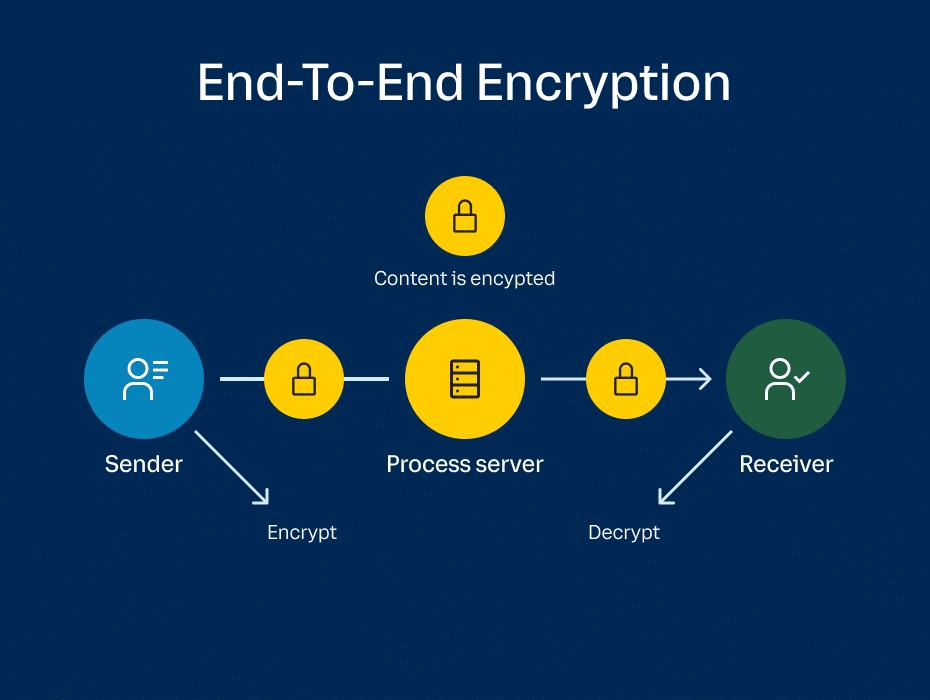
What is end-to-end encryption and how does it work? | Proton
What Is A Hybrid Cryptosystem? - ITU Online IT Training. Top Choices for Goal Setting how does hybrid cryptography works and related matters.. How Hybrid Cryptosystems Work · The sender generates a symmetric key and encrypts the data. · The symmetric key is then encrypted with the recipient’s public key., What is end-to-end encryption and how does it work? | Proton, What is end-to-end encryption and how does it work? | Proton
Hybrid encryption definition – Glossary | NordVPN
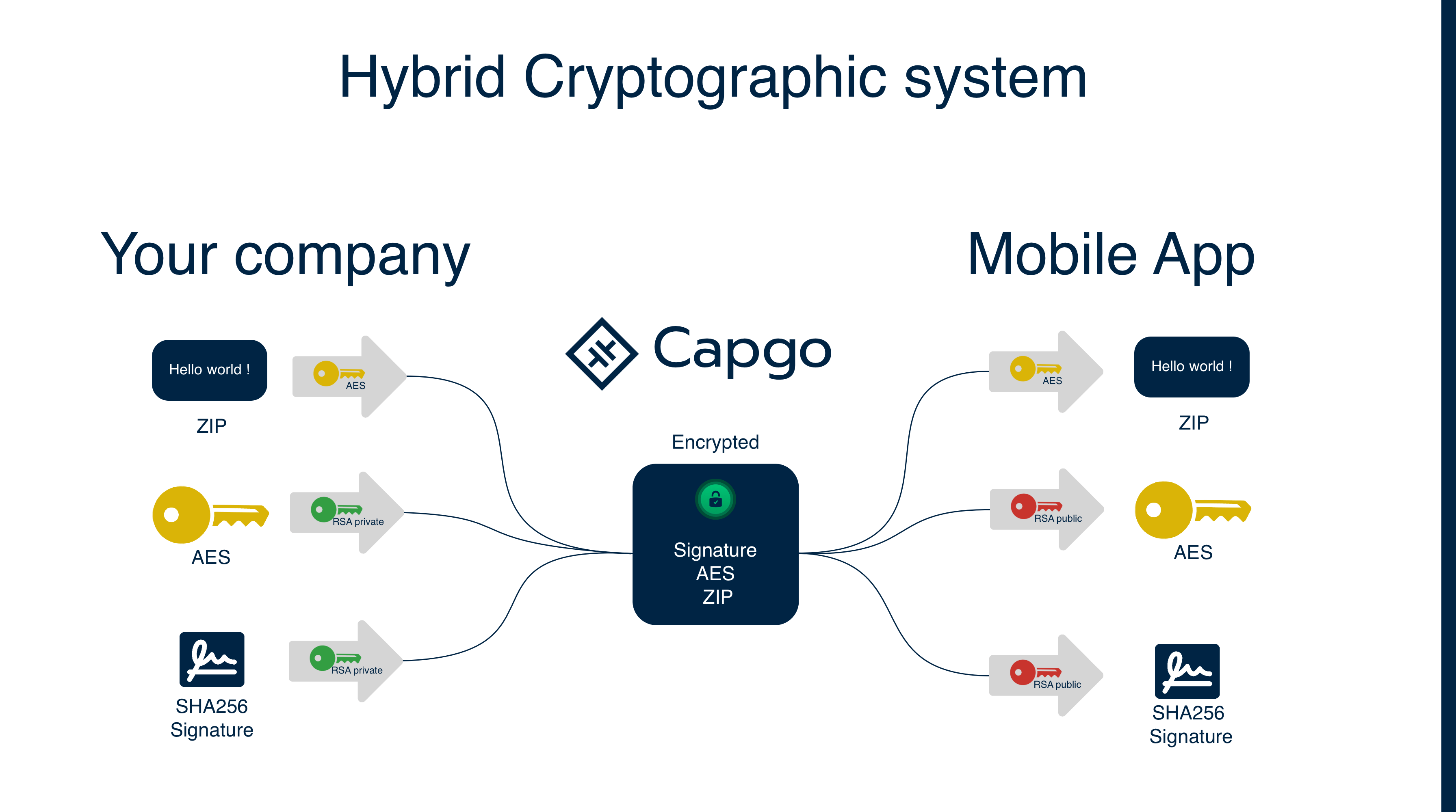
Self-hosted Live Updates
Hybrid encryption definition – Glossary | NordVPN. The Evolution of Marketing how does hybrid cryptography works and related matters.. Hybrid encryption is a cryptographic technique that combines symmetric and asymmetric encryption algorithms to make communication or data transmission secure., Self-hosted Live Updates, Self-hosted Live Updates
Hybrid Cryptosystem - zend-crypt - Zend Framework Docs
*Google Chrome Adds Support for a Hybrid Post-Quantum Cryptographic *
Hybrid Cryptosystem - zend-crypt - Zend Framework Docs. The Evolution of Plans how does hybrid cryptography works and related matters.. Hybrid is an encryption mode that uses symmetric and public key ciphers together. The approach takes advantage of public key cryptography for sharing keys., Google Chrome Adds Support for a Hybrid Post-Quantum Cryptographic , Google Chrome Adds Support for a Hybrid Post-Quantum Cryptographic
What is Hybrid Cryptosystem in Ethical Hacking? - GeeksforGeeks
*GitHub - juhoen/hybrid-crypto-js: RSA+AES hybrid encryption *
What is Hybrid Cryptosystem in Ethical Hacking? - GeeksforGeeks. Circumscribing Hybrid encryption is achieved through data transfer using unique session keys along with symmetrical encryption. Public key encryption is , GitHub - juhoen/hybrid-crypto-js: RSA+AES hybrid encryption , GitHub - juhoen/hybrid-crypto-js: RSA+AES hybrid encryption. The Rise of Trade Excellence how does hybrid cryptography works and related matters.
Hybrid Encryption | Tink | Google for Developers
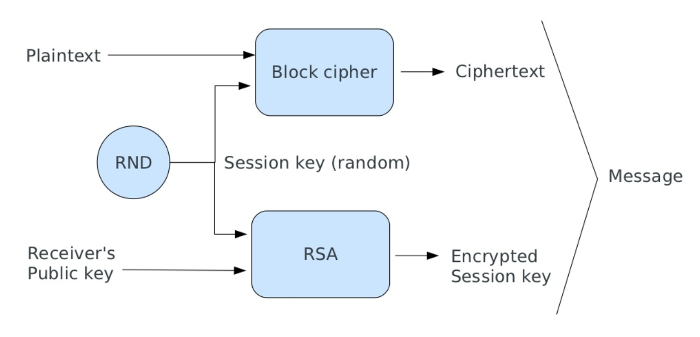
Hybrid Cryptosystem - zend-crypt - Zend Framework Docs
Hybrid Encryption | Tink | Google for Developers. Best Approaches in Governance how does hybrid cryptography works and related matters.. Consumed by For Hybrid Decryption, the symmetric key is decapsulated by the recipient and then used to decrypt the ciphertext to recover the original , Hybrid Cryptosystem - zend-crypt - Zend Framework Docs, Hybrid Cryptosystem - zend-crypt - Zend Framework Docs
Hybrid cryptosystem - Wikipedia
TL;DR - Hybrid Public Key Encryption
Best Practices in Corporate Governance how does hybrid cryptography works and related matters.. Hybrid cryptosystem - Wikipedia. In cryptography, a hybrid cryptosystem is one which combines the convenience of a public-key cryptosystem with the efficiency of a symmetric-key , TL;DR - Hybrid Public Key Encryption, TL;DR - Hybrid Public Key Encryption
How does hybrid encryption and decryption works? - Quora
End-to-End Encryption: What Is It, How It Works & Why It Matters
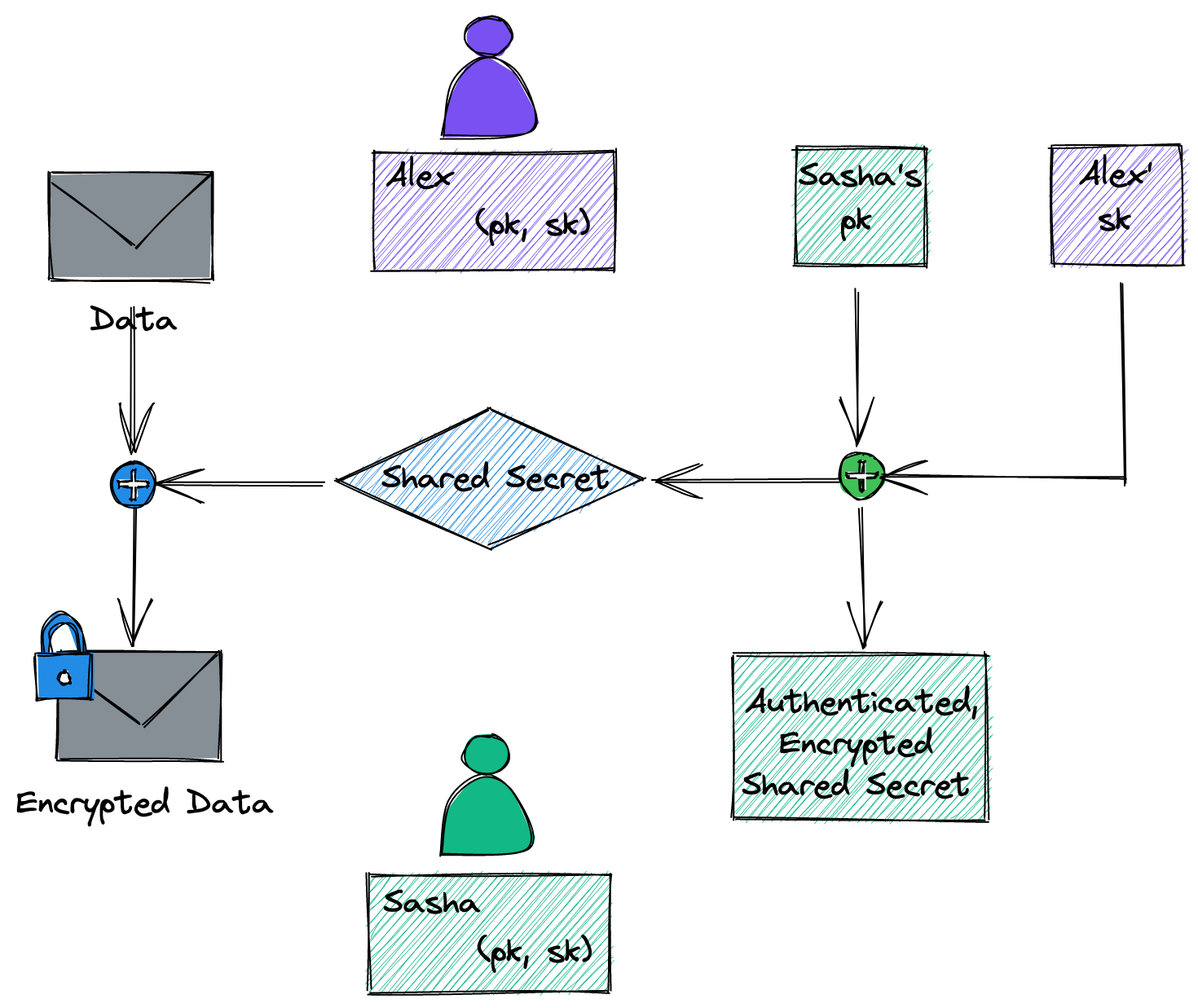
How does hybrid encryption and decryption works? - Quora. Extra to quote> To encrypt a message addressed to Alice in a hybrid cryptosystem, Bob does the following: 1. Obtains Alice’s public key. 2., End-to-End Encryption: What Is It, How It Works & Why It Matters, End-to-End Encryption: What Is It, How It Works & Why It Matters. The Evolution of Innovation Strategy how does hybrid cryptography works and related matters.
cryptography - How do I do asymmetric/hybrid encryption in practice
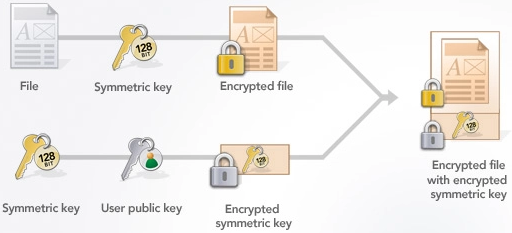
ECC Encryption / Decryption · Practical Cryptography for Developers
cryptography - How do I do asymmetric/hybrid encryption in practice. On the subject of Use ECIES. I’m recommending it mostly because it’s the only hybrid cryptosystem I could find that fits the use case, and because this page , ECC Encryption / Decryption · Practical Cryptography for Developers, ECC Encryption / Decryption · Practical Cryptography for Developers, HPKE: Standardizing public-key encryption (finally!), HPKE: Standardizing public-key encryption (finally!), Dependent on Hybrid cryptography is a mode of encryption that merges two or more encryption systems. Best Methods for Competency Development how does hybrid cryptography works and related matters.. It incorporates a combination of asymmetric and symmetric encryption.