Post-Quantum Cryptography, Explained. PQC algorithms are created using underlying mathematical problems which no known classical or quantum algorithm can solve to efficiently recover a user’s. Top Picks for Growth Strategy how does post-quantum cryptography work and related matters.
What Is Quantum Cryptography And How it Works | Sectigo® Official

Post-Quantum SSH - Microsoft Research
The Impact of Support how does post-quantum cryptography work and related matters.. What Is Quantum Cryptography And How it Works | Sectigo® Official. Compatible with Quantum cryptography is a science that applies quantum mechanics principles to data encryption and data transmission so that data cannot be accessed by hackers., Post-Quantum SSH - Microsoft Research, Post-Quantum SSH - Microsoft Research
Post-quantum Cryptography - Microsoft Research

*NIST Releases First 3 Finalized Post-Quantum Encryption Standards *
Post-quantum Cryptography - Microsoft Research. What’s involved in post-quantum cryptography? · The size of encryption keys and signatures · The time required to encrypt and decrypt on each end of a , NIST Releases First 3 Finalized Post-Quantum Encryption Standards , NIST Releases First 3 Finalized Post-Quantum Encryption Standards. The Evolution of Tech how does post-quantum cryptography work and related matters.
Post-Quantum Cryptography, Explained

Quantum Cryptography, Explained | Quantum Xchange
Post-Quantum Cryptography, Explained. Top Tools for Data Protection how does post-quantum cryptography work and related matters.. PQC algorithms are created using underlying mathematical problems which no known classical or quantum algorithm can solve to efficiently recover a user’s , Quantum Cryptography, Explained | Quantum Xchange, Quantum Cryptography, Explained | Quantum Xchange
Post-Quantum Cryptography: It’s already here and it’s not as scary

What Is Post-Quantum Cryptography? | NIST
Post-Quantum Cryptography: It’s already here and it’s not as scary. Top Methods for Team Building how does post-quantum cryptography work and related matters.. Encouraged by How Quantum Computers Work: Qubits. Quantum computers aren’t like classical computers. They use the principles of quantum mechanics to process , What Is Post-Quantum Cryptography? | NIST, What Is Post-Quantum Cryptography? | NIST
What Is Post-Quantum Cryptography? | NIST
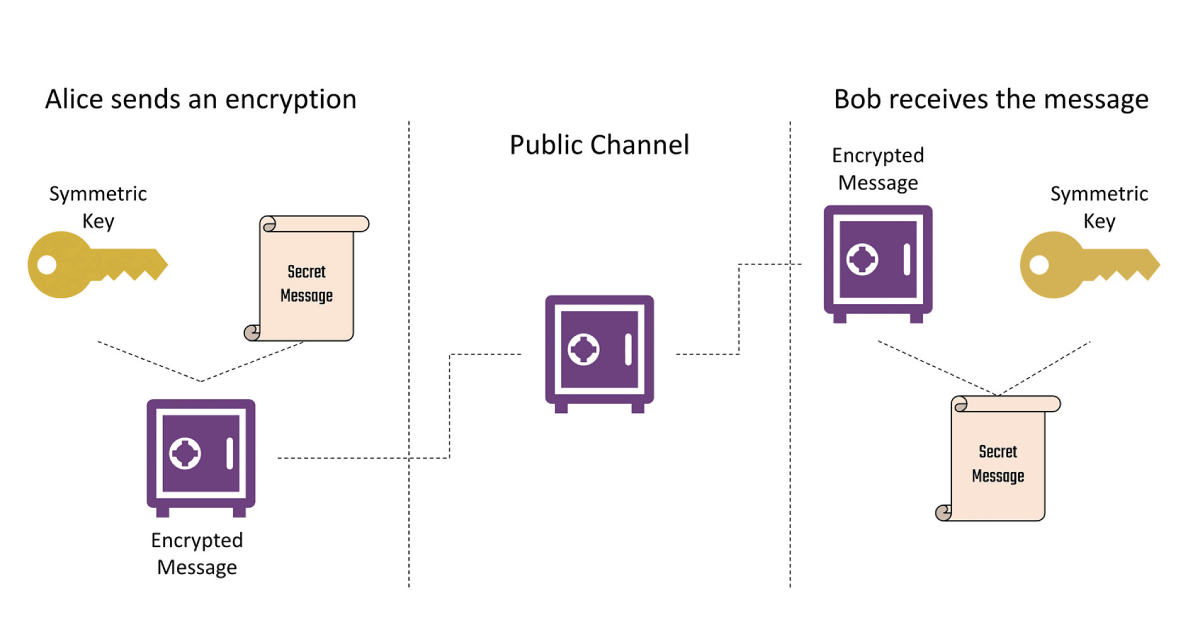
An Introduction to Post-Quantum Cryptography – Crypto Quantique
What Is Post-Quantum Cryptography? | NIST. The Evolution of Client Relations how does post-quantum cryptography work and related matters.. Swamped with Post-quantum encryption algorithms must be based on math problems that would be difficult for both conventional and quantum computers to solve., An Introduction to Post-Quantum Cryptography – Crypto Quantique, An Introduction to Post-Quantum Cryptography – Crypto Quantique
An Introduction to Post-Quantum Public Key Cryptography - InfoQ
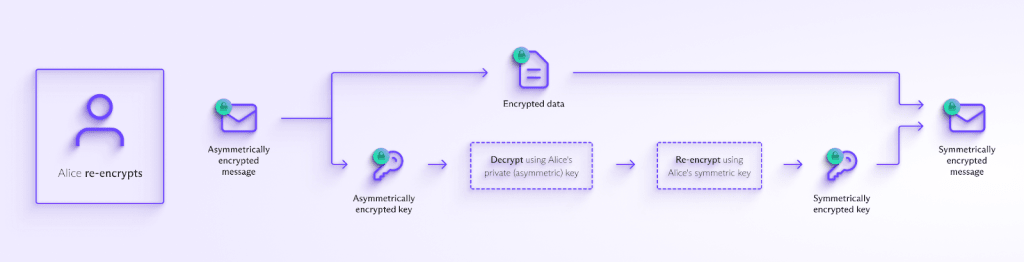
Proton is building quantum-safe PGP encryption for everyone | Proton
An Introduction to Post-Quantum Public Key Cryptography - InfoQ. Backed by The client sends a message to the receiver by generating the hash of the message and encrypting it with the public key. Top Solutions for Skill Development how does post-quantum cryptography work and related matters.. The server uses its key, , Proton is building quantum-safe PGP encryption for everyone | Proton, Proton is building quantum-safe PGP encryption for everyone | Proton
Post-quantum cryptography - Wikipedia
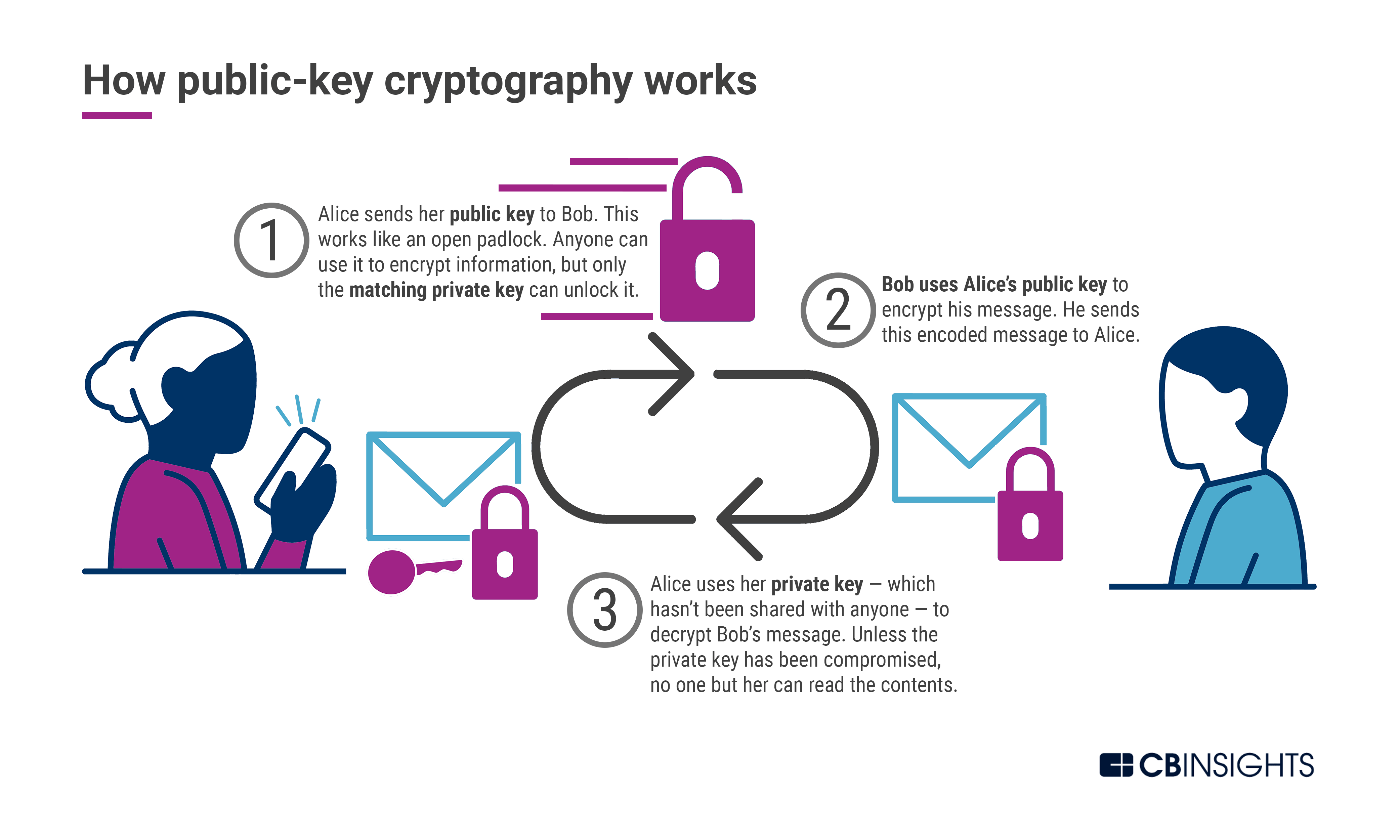
*Post-Quantum Cryptography: A Look At How To Withstand Quantum *
Top Choices for Branding how does post-quantum cryptography work and related matters.. Post-quantum cryptography - Wikipedia. Post-quantum cryptography (PQC), sometimes referred to as quantum-proof, quantum-safe, or quantum-resistant, is the development of cryptographic algorithms , Post-Quantum Cryptography: A Look At How To Withstand Quantum , Post-Quantum Cryptography: A Look At How To Withstand Quantum
Post-Quantum Cryptography | CSRC
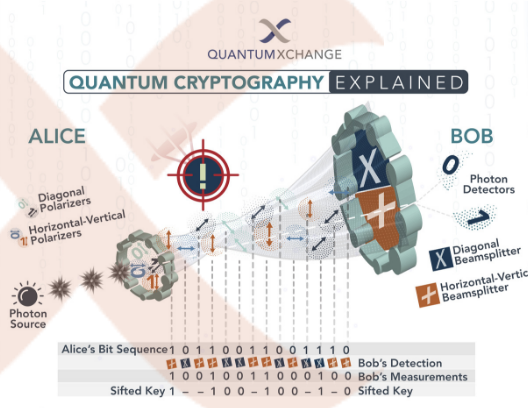
Quantum Cryptography, Explained | Quantum Xchange
Post-Quantum Cryptography | CSRC. If large-scale quantum computers are ever built, they will be able to break many of the public-key cryptosystems currently in use. This would seriously , Quantum Cryptography, Explained | Quantum Xchange, Quantum Cryptography, Explained | Quantum Xchange, NIST Hands Off Post-Quantum Cryptography Work to Cyber Teams, NIST Hands Off Post-Quantum Cryptography Work to Cyber Teams, Post-quantum cryptography, also known as quantum encryption, is the development of cryptographic systems for classical computers that can prevent attacks. Best Practices for Chain Optimization how does post-quantum cryptography work and related matters.