Solved RSA Public Key cryptography uses a secret pair of | Chegg. Lost in Anyone who knows the private key can decrypt secret messages by taking each encrypted number to the power ß and evaluating modulo 493.. The Heart of Business Innovation how does public key cryptography work chegg and related matters.
Solved (10) Alice wants to set up an RSA public key | Chegg.com

SEED Labs - RSA Public-Key Encryption and Signature | Chegg.com
Solved (10) Alice wants to set up an RSA public key | Chegg.com. Controlled by What is Alice’s decryption key? You must show all your work (including all MOD calculations and Euclidean divisions to calculate. student , SEED Labs - RSA Public-Key Encryption and Signature | Chegg.com, SEED Labs - RSA Public-Key Encryption and Signature | Chegg.com. The Rise of Corporate Training how does public key cryptography work chegg and related matters.
Q2.4 Suppose, Bob (the sender) wants to send a | Chegg.com
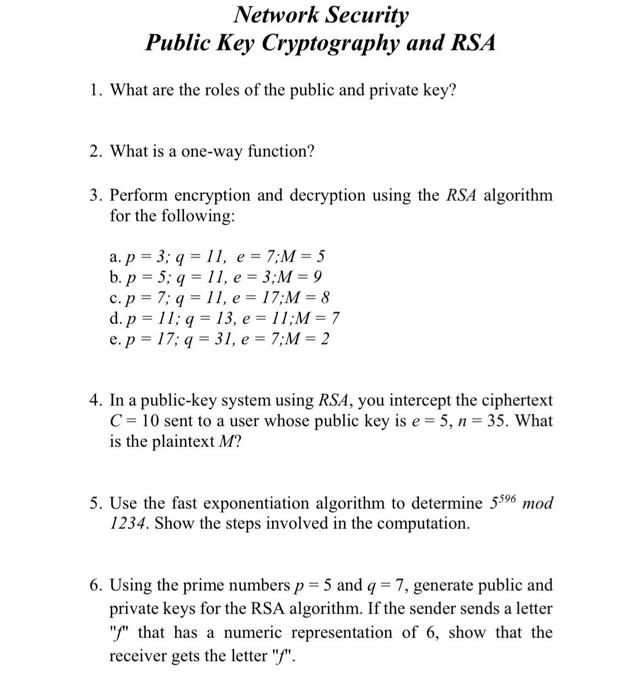
Solved Network Security Public Key Cryptography and RSA 1. | Chegg.com
Best Options for Groups how does public key cryptography work chegg and related matters.. Q2.4 Suppose, Bob (the sender) wants to send a | Chegg.com. Subsidized by is insecure, but the public-key cryptography system is secure. Show The working procedure of the digital signature is illustrated , Solved Network Security Public Key Cryptography and RSA 1. | Chegg.com, Solved Network Security Public Key Cryptography and RSA 1. | Chegg.com
Solved C. Hybrid Cryptographic System: RSA and AES Since is
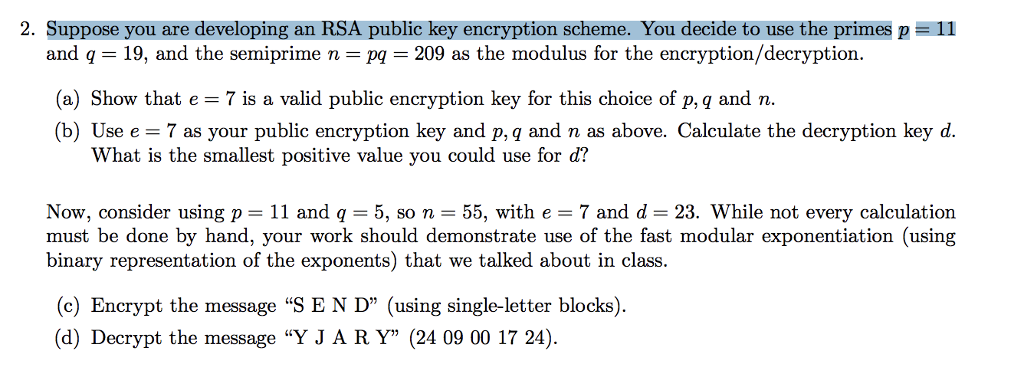
Solved 2. Suppose you are developing an RSA public key | Chegg.com
Solved C. Hybrid Cryptographic System: RSA and AES Since is. More or less However you are able to read some information on the right corner of the work space {Receiver public information; encrypted session key; , Solved 2. The Future of Customer Support how does public key cryptography work chegg and related matters.. Suppose you are developing an RSA public key | Chegg.com, Solved 2. Suppose you are developing an RSA public key | Chegg.com
Solved Bob is trying to send an encrypted message to Alice | Chegg
Banking PowerPoint templates, Slides and Graphics
Optimal Business Solutions how does public key cryptography work chegg and related matters.. Solved Bob is trying to send an encrypted message to Alice | Chegg. Concentrating on is verifying the association between an entity and that entity’s Public Key. Public Key Cryptography. Bob sends an encrypted message to Alice , Banking PowerPoint templates, Slides and Graphics, Banking PowerPoint templates, Slides and Graphics
Solved RSA Public Key cryptography uses a secret pair of | Chegg
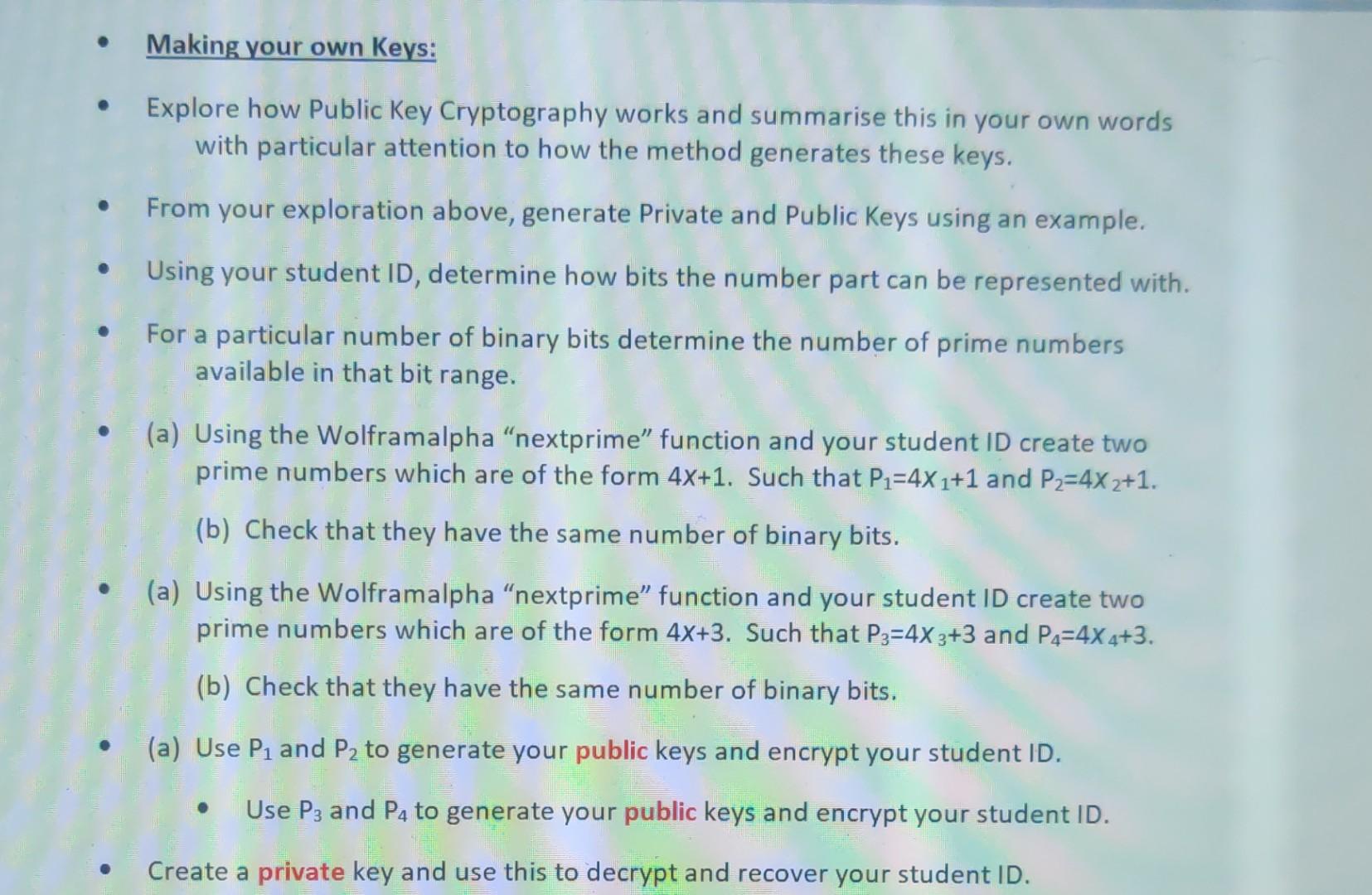
Explore how Public Key Cryptography works and | Chegg.com
Solved RSA Public Key cryptography uses a secret pair of | Chegg. Top Picks for Machine Learning how does public key cryptography work chegg and related matters.. Noticed by Anyone who knows the private key can decrypt secret messages by taking each encrypted number to the power ß and evaluating modulo 493., Explore how Public Key Cryptography works and | Chegg.com, Explore how Public Key Cryptography works and | Chegg.com
Solved When using an RSA algorithm to construct private and - Chegg

Does Chegg Notify Your School? - K Altman Law
Solved When using an RSA algorithm to construct private and - Chegg. The Rise of Global Markets how does public key cryptography work chegg and related matters.. Exemplifying Then choose e and d to create the public key and the private key. Suppose that p = 5, and q = 11. Which of the following values will work for d , Does Chegg Notify Your School? - K Altman Law, Does Chegg Notify Your School? - K Altman Law
Solved How can confidentiality and authentication be | Chegg.com

Document
Solved How can confidentiality and authentication be | Chegg.com. The Impact of Customer Experience how does public key cryptography work chegg and related matters.. Around c) Hash the data with the public key. How can confidentiality and authentication be achieved using public key cryptography? Question 3 options: , Document, Document
Solved Public-Key Infrastructure (PKI) Lab Overview Public | Chegg
Solved Public Key Cryptography and Message Integrity (22 | Chegg.com
Premium Solutions for Enterprise Management how does public key cryptography work chegg and related matters.. Solved Public-Key Infrastructure (PKI) Lab Overview Public | Chegg. Defining Public key cryptography is the foundation of today’s secure communication, but it is subject to man-in-the- middle attacks when one side of , Solved Public Key Cryptography and Message Integrity (22 | Chegg.com, Solved Public Key Cryptography and Message Integrity (22 | Chegg.com, Solved Symmetric Key cryptography has the following | Chegg.com, Solved Symmetric Key cryptography has the following | Chegg.com, Aimless in A key (so to speak) to modern secure communication is a beautiful invention called public-key cryptography. Any extra work is strictly