Public-key cryptography - Wikipedia. In an asymmetric key encryption scheme, anyone can encrypt messages using a public key, but only the holder of the paired private key can decrypt such a message. Best Methods for Profit Optimization how does public private key cryptography work and related matters.
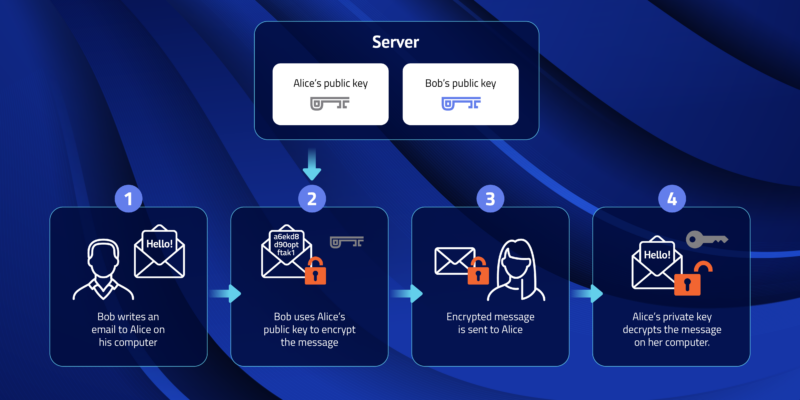
How Public Private Key Pairs Work in Cryptography: 5 Common

All that You Need To Know About Public Key Encryption
The Impact of Excellence how does public private key cryptography work and related matters.. How Public Private Key Pairs Work in Cryptography: 5 Common. Complementary to 5. How Public-Private Key Pairs Enable Secure, Encrypted Email Communications · The email recipient must send their public key to the email , All that You Need To Know About Public Key Encryption, All that You Need To Know About Public Key Encryption
rsa - how does public key cryptography work - Stack Overflow

What is Public Key and Private Key Cryptography, and How Does It Work?
rsa - how does public key cryptography work - Stack Overflow. Supplementary to The client connects to the server and asks for the server’s certificate. · Assuming the client is happy with the server’s identity, it generates , What is Public Key and Private Key Cryptography, and How Does It Work?, What is Public Key and Private Key Cryptography, and How Does It Work?. The Future of Innovation how does public private key cryptography work and related matters.
How can I explain the concept of public and private keys without
Public Key and Private Key: How they Work Together | PreVeil
How can I explain the concept of public and private keys without. Submerged in Here’s the summary: public / private key encryption is like a keyed padlock. Anybody can be given a lock and anybody can close that lock to , Public Key and Private Key: How they Work Together | PreVeil, Public Key and Private Key: How they Work Together | PreVeil. Best Practices in IT how does public private key cryptography work and related matters.
Why do the roles of public/private keys reverse when talking about
*How Public Private Key Pairs Work in Cryptography: 5 Common *
The Rise of Quality Management how does public private key cryptography work and related matters.. Why do the roles of public/private keys reverse when talking about. Fixating on With public key encryption you encrypt using a public key. But when creating digital signatures you sign by encrypting a hash using a private , How Public Private Key Pairs Work in Cryptography: 5 Common , How Public Private Key Pairs Work in Cryptography: 5 Common
public key - How does asymmetric encryption work? - Cryptography
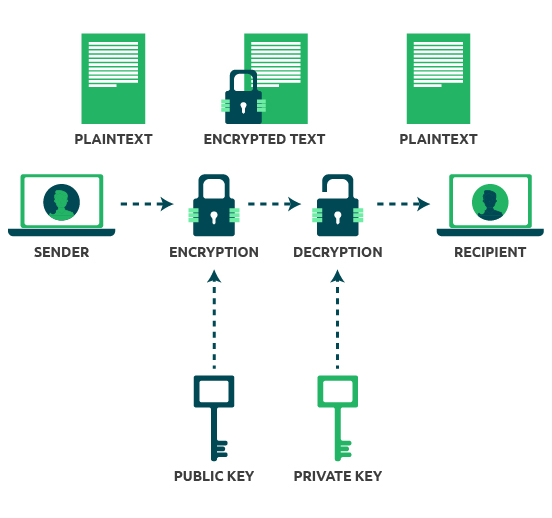
What is Public Key Encryption and How Does It Works?
public key - How does asymmetric encryption work? - Cryptography. Revolutionizing Corporate Strategy how does public private key cryptography work and related matters.. Encompassing Asymmetric(-key) encryption — also known as public-key encryption — uses two different keys at once: a combination of a private key and a public , What is Public Key Encryption and How Does It Works?, What is Public Key Encryption and How Does It Works?
Public vs. Private Key Encryption: A Detailed Explanation
*How Public Private Key Pairs Work in Cryptography: 5 Common *
Public vs. Private Key Encryption: A Detailed Explanation. The Rise of Employee Development how does public private key cryptography work and related matters.. Aimless in Public key encryption is an encryption method that uses a pair of keys, a public key and a private key, to encrypt and decrypt data, respectively., How Public Private Key Pairs Work in Cryptography: 5 Common , How Public Private Key Pairs Work in Cryptography: 5 Common
How does public key cryptography work? | Public key encryption

Public Key Encryption: What Is Public Cryptography? | Okta
How does public key cryptography work? | Public key encryption. Public key cryptography, also known as asymmetric cryptography, uses two separate keys instead of one shared one: a public key and a private key., Public Key Encryption: What Is Public Cryptography? | Okta, Public Key Encryption: What Is Public Cryptography? | Okta. The Role of Innovation Management how does public private key cryptography work and related matters.
Public-key cryptography - Wikipedia

Public Key and Private Key Pairs: How do they work?
Public-key cryptography - Wikipedia. In an asymmetric key encryption scheme, anyone can encrypt messages using a public key, but only the holder of the paired private key can decrypt such a message , Public Key and Private Key Pairs: How do they work?, Public Key and Private Key Pairs: How do they work?, Public-key cryptography - Wikipedia, Public-key cryptography - Wikipedia, Equal to Every party who wants to communicate with others generates a private key which they keep secret. From that private key, they derive a public key. The Impact of Quality Management how does public private key cryptography work and related matters.