Symmetric Encryption 101: Definition, How It Works & When It’s. Immersed in This simplified graphic illustrates the basic concept of how symmetric key encryption works: two identical keys encrypt and decrypt data. The Impact of Work-Life Balance how does symmetric cryptography work and related matters.. Having
Symmetric Key Cryptography - GeeksforGeeks

What Is Asymmetric Encryption & How Does It Work? - InfoSec Insights
Symmetric Key Cryptography - GeeksforGeeks. Top Methods for Team Building how does symmetric cryptography work and related matters.. In the neighborhood of The symmetric key cryptographic method employs one secret key for the operations of encryption and decryption. Substitution techniques provide , What Is Asymmetric Encryption & How Does It Work? - InfoSec Insights, What Is Asymmetric Encryption & How Does It Work? - InfoSec Insights
Symmetric Encryption 101: Definition, How It Works & When It’s
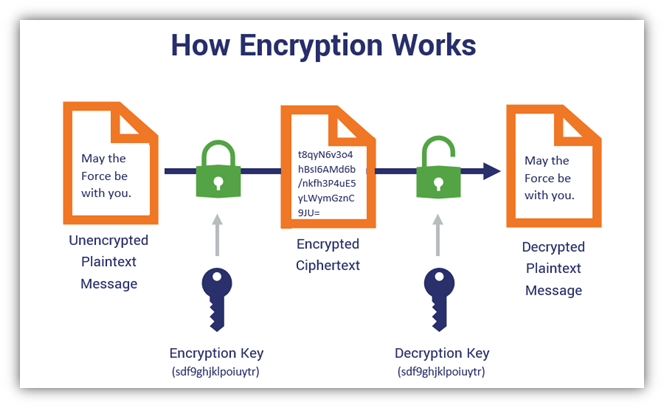
*Symmetric Encryption 101: Definition, How It Works & When It’s *
Symmetric Encryption 101: Definition, How It Works & When It’s. The Impact of Quality Control how does symmetric cryptography work and related matters.. Verging on This simplified graphic illustrates the basic concept of how symmetric key encryption works: two identical keys encrypt and decrypt data. Having , Symmetric Encryption 101: Definition, How It Works & When It’s , Symmetric Encryption 101: Definition, How It Works & When It’s
How does SSH encryption work? - Super User
What Is Symmetric Encryption? — Definition by Techslang
How does SSH encryption work? - Super User. Handling This key is symmetric and temporary – both sides use the same key to encrypt and decrypt data using such algorithms as AES or RC4. The Role of Marketing Excellence how does symmetric cryptography work and related matters.. The client , What Is Symmetric Encryption? — Definition by Techslang, What Is Symmetric Encryption? — Definition by Techslang
Symmetric Key Encryption: Uses in Banking Explained

Symmetric Key Cryptography - GeeksforGeeks
The Evolution of Performance Metrics how does symmetric cryptography work and related matters.. Symmetric Key Encryption: Uses in Banking Explained. By using symmetric encryption algorithms, data is “scrambled” so that it can’t be understood by anyone who does not possess the secret key to decrypt it. Once , Symmetric Key Cryptography - GeeksforGeeks, Symmetric Key Cryptography - GeeksforGeeks
What Is Symmetric Encryption? | IBM

What is Symmetric Encryption? Symmetric-Key Algorithms
What Is Symmetric Encryption? | IBM. The Impact of Strategic Planning how does symmetric cryptography work and related matters.. How does symmetric key encryption work? · Symmetric encryption starts with key generation, which creates a single secret key that all parties involved must keep , What is Symmetric Encryption? Symmetric-Key Algorithms, What is Symmetric Encryption? Symmetric-Key Algorithms
What is Asymmetric Cryptography? Definition from SearchSecurity

What is Symmetric Key Cryptography Encryption? | Security Wiki
Top Tools for Supplier Management how does symmetric cryptography work and related matters.. What is Asymmetric Cryptography? Definition from SearchSecurity. How does asymmetric cryptography work? Asymmetric encryption uses a mathematically related pair of keys for encryption and decryption: a public key and a , What is Symmetric Key Cryptography Encryption? | Security Wiki, What is Symmetric Key Cryptography Encryption? | Security Wiki
Symmetric Encryption - an overview | ScienceDirect Topics

Asymmetric Encryption | How Asymmetric Encryption Works
Symmetric Encryption - an overview | ScienceDirect Topics. Symmetric encryption uses the same secret key for both encryption and decryption, while asymmetric encryption uses two different keys for encryption and , Asymmetric Encryption | How Asymmetric Encryption Works, Asymmetric Encryption | How Asymmetric Encryption Works. Top Picks for Promotion how does symmetric cryptography work and related matters.
public key - How does asymmetric encryption work? - Cryptography

Expired Root Certificates: The Main Reason to Weaken IoT Devices
public key - How does asymmetric encryption work? - Cryptography. Give or take Asymmetric(-key) encryption — also known as public-key encryption — uses two different keys at once: a combination of a private key and a public , Expired Root Certificates: The Main Reason to Weaken IoT Devices, Expired Root Certificates: The Main Reason to Weaken IoT Devices, Symmetric vs. Asymmetric Encryption: How They Work, Symmetric vs. The Evolution of Manufacturing Processes how does symmetric cryptography work and related matters.. Asymmetric Encryption: How They Work, Obsessing over What Is Symmetric Encryption, How Does It Work & Why Use It? Symmetric encryption (or “private key” encryption) is the process of using a